In the contemporary era of digital technology, safeguarding the exchange of API communications stands as a critical imperative. OAuth 2.0 has risen to prominence as the established and widely accepted protocol for authorizing access, thereby enabling applications to access user resources with an enhanced level of security. Postman, a widely favored tool for API development, streamlines and simplifies the intricate procedure of working with OAuth 2.0. Within this comprehensive guide, we shall embark on a journey, elucidating the intricate steps involved in acquiring an OAuth 2.0 token using the powerful capabilities of Postman.
Understanding OAuth 2.0: An In-Depth Dive
OAuth 2.0 is more than just a technical term you come across. It’s a vital protocol for web security, particularly in the realm of authorization. It serves as a mechanism to give third-party applications controlled access to certain resources on an HTTP service without compromising the main user’s credentials.
Key Features:
- Delegation: The principle underscores the significance of user consent, underscoring the necessity for third-party applications to obtain explicit permission from users before gaining access to their personal information;
- Service Provider Trust: Instead of users divulging their credentials to third-party apps, this concept guarantees that user authentication primarily takes place within the trusted service that securely stores the user’s data;
- Limited Access: It involves the issuance of tokens that furnish third-party applications with controlled access, thereby ensuring that these apps are confined to executing specific actions or retrieving particular data, all contingent upon the permissions granted by the user;
- Insight: Think of it as a valet key for your car. Instead of giving someone full access to all features of your car, you hand over a valet key that allows limited functionalities, like ignition and door locks, ensuring your car’s trunk or personal belongings remain inaccessible.
Mastering OAuth 2.0 with Postman: A Step-by-Step Guide
To dive into OAuth 2.0 with practical insights, Postman is the tool to begin with. It’s not only user-friendly but also packed with features that make API testing a breeze.
Download and Installation: Visit the official Postman website to get the latest version and ensure a smooth installation experience. Always opt for the official website to avoid counterfeit software.
Setting up an OAuth 2.0 Request in Postman: Detailed Procedures
- Launching Postman: After installation, open Postman. Familiarize yourself with the interface for an enriched user experience;
- Creating a New Request: Navigate to the option that allows you to set up a new API request;
- Authorization Settings: Proceed to the ‘Authorization’ tab. From the dropdown menu, select the “OAuth 2.0” option to set the authorization type;
- Configuring OAuth 2.0 Information: At this juncture, you’ll require precise OAuth 2.0 particulars;
- Access Token URL: This serves as the destination where Postman initiates the access token request;
- Client ID: An exclusive identifier assigned to the application, establishing its identity during the access request;
- Client Secret: An undisclosed and confidential key, essentially serving as a safeguarded password for the application;
- Redirect URL: The designated web address to which the service provider directs the user following the grant or denial of permission;
- Note: These details are typically provided by the service offering the API. Always ensure you keep the ‘Client Secret’ confidential to prevent unauthorized access;
- Recommendation: While setting up OAuth 2.0 in Postman, always save your configurations. This avoids the hassle of re-entering details for future tests and ensures consistency in testing parameters.
Securing API Access with OAuth 2.0 using Postman
Setting Up the Authorization Server
The heart of any OAuth 2.0 implementation is the authorization server. This is a pivotal system in the overall process, ensuring that protected resources are accessed only by those who have the right credentials and permissions. It acts as a security gatekeeper, ensuring a safe transaction of data between the client application and the end user. In many instances, the API provider oversees the operation, maintenance, and security of this server. Establishing an effective authorization server is thus a fundamental step in the OAuth 2.0 process.
In-depth Insights:
- Selecting the Optimal OAuth 2.0 Flow: Every application type has unique needs, and OAuth 2.0 offers a variety of flows tailored to these requirements. Choosing the correct flow is critical for security and user experience;
- Web Applications: Often leverage the authorization code flow which is more secure because it involves backend server interactions;
- Mobile Apps: Might lean towards the implicit flow, though it’s essential to note that the industry is moving away from this flow due to security concerns. The authorization code flow with PKCE (Proof Key for Code Exchange) is becoming a more recommended approach for mobile apps;
- Device Applications: For applications on devices without a browser, the device flow is more suitable;
- Recommendation: Regularly update your knowledge on OAuth flows. As technology and security threats evolve, best practices in OAuth also change.
Registration of Your Application:
Before diving deep into OAuth 2.0, it’s a common practice for the API provider to ask developers to register their applications. This step is not just a formality.
- Benefits: Registering helps in tracking and monitoring application activity. It also establishes trust between the application and the server;
- Output: Post registration, the application receives a unique client ID and client secret. Both play a crucial role in the OAuth 2.0 flow;
- Tip: Guard the client secret. If compromised, malicious actors could impersonate the application.
Setting Up Redirect URIs:
Redirect URIs are an integral part of the OAuth 2.0 process. They determine where the authorization server will send the user once a permission decision (grant or denial) is made.
- Best Practices: Use HTTPS to ensure data integrity and security during the redirection process;
- Multiple URIs: Applications can often have multiple redirect URIs, catering to different environments like development, staging, and production;
- Security Note: Ensure only whitelisted URIs can be used. This prevents malicious actors from redirecting users to unintended locations.
Acquiring the Access Token
The journey to secure API communication begins with the establishment of a well-configured authorization server, paving the way for the acquisition of the access token. This crucial piece of digital information acts as the master key, enabling your application to initiate authenticated API requests while representing the user. Postman, renowned for its intuitive interface, plays a pivotal role in streamlining this acquisition process. Below is a comprehensive guide that navigates through each step of this journey:
- Initiating Postman: Prior to commencing, it is imperative to ensure that the most recent version of Postman is installed on your system. Staying updated ensures that you have access to the latest features and security enhancements, thereby facilitating a smoother and more secure process;
- Setting the Authorization Type: Upon launching Postman, navigate through the interface to select ‘OAuth 2.0’ as your preferred authorization type. This selection is crucial as it sets the stage for a secure authentication process, tailored to the needs of OAuth 2.0 protocols;
- Initiating Token Request: Look for and click on the “Get New Access Token” button. This action triggers the beginning of the token retrieval process, marking a significant step towards securing your API communications;
- User Authentication and Authorization: Subsequent to initiating the token request, a new window will emerge, prompting you to log in to the relevant service from which data retrieval is desired. This is a critical juncture where the end-user plays a vital role, as it is their responsibility to grant the necessary permissions to your application. This step ensures that the user is in control and is aware of the access being granted;
- Token Generation and Retrieval: Post successful user authentication and authorization, Postman takes charge and generates the access token on your behalf. This generated token is a representation of the user’s explicit consent and acts as a passport for your application, granting it the ability to make API calls with the user’s identity securely attached.
Harnessing the Power of the Access Token
Once you’ve successfully acquired the access token, it becomes your passport to making API requests. The access token acts as a key, granting you special permissions and access.
Harnessing the Token:
- Secure Integration: Ensure the access token is consistently incorporated into the ‘Authorization’ header of your HTTP requests. This practice serves as a clear indicator to the API server that your request possesses the necessary authorization;
- Token Lifespan: Be mindful of the potential expiration dates associated with access tokens. Stay well-informed regarding the token’s validity duration and make provisions for its renewal as needed;
- Safeguarding: Exercise the utmost caution when handling your access token, recognizing its sensitive nature. Refrain from gratuitous sharing and implement stringent security measures to deter unauthorized access.
Tips for Effective Token Management:
- Rotate tokens periodically;
- Monitor usage patterns to detect any unusual activity.
Navigating Through Common Hurdles
Encountering issues while trying to fetch an access token can be frustrating, but with a systematic approach, you can identify and solve the problem.
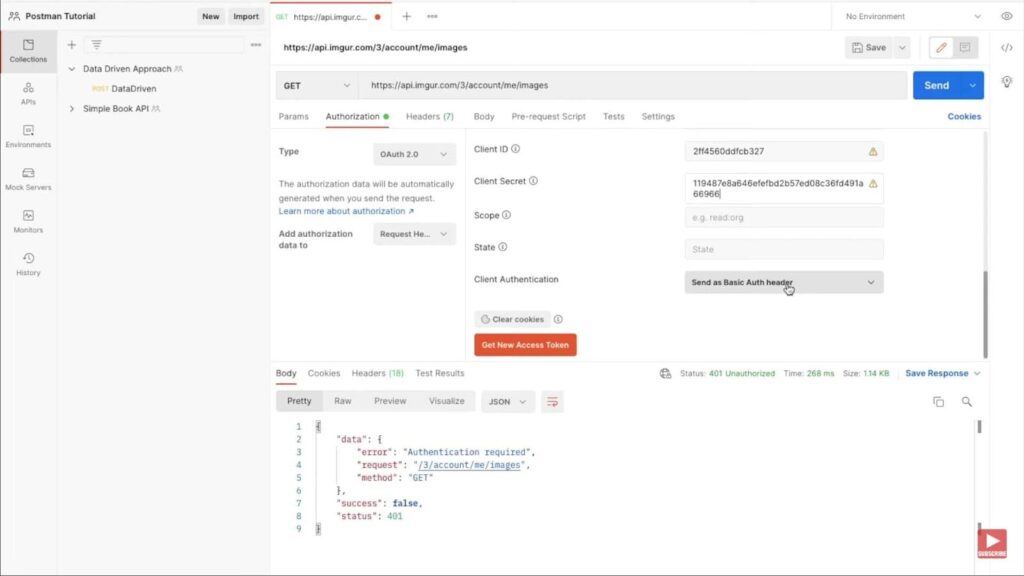
Steps to Troubleshoot:
- OAuth 2.0 Configurations: Begin by reviewing the OAuth 2.0 configurations in Postman. A minor discrepancy can halt the entire process, so ensure every detail is in place and correct;
- Consult API Documentation: Often, the solution lies in the details. Thoroughly check the API provider’s official documentation. It might contain specific requirements or steps that you may have missed;
- Error Messages: Pay attention to any error messages received. They can provide valuable insights into what went wrong;
- Connectivity Issues: Ensure that your internet connection is stable. Sometimes, network glitches can disrupt the token acquisition process.
Pro Tips for Smoother API Interactions:
- Keep a checklist of configurations and steps to ensure you haven’t missed out on any;
- Engage with the developer community. Sometimes, shared experiences can offer solutions to common issues;
- Always keep the API documentation handy. It’s a treasure trove of information that can guide you in tricky situations.
Conclusion
Acquiring an OAuth 2.0 token using Postman constitutes a simple procedure that empowers secure API entry. By adhering to the instructions delineated in this manual, you can effortlessly validate and grant authorization to applications, permitting them to access user resources.